关于内网“间谍”设备(F-BOMB)的介绍: 2012年1月28号一篇关于DARPA(Defense Advanced Research Projects Agency)资助的网络间谍设备的新闻轰动一时,从新闻当中我们可以得知,DARPA赞助了CTF的”Reticle: Leaderless Command and Control”,从而F-BOMB也跟着DARPA的赞助浮现出了水面。
0x01 作战准备: 1.TP-LINK MR3040 2.SanDisk的酷豆系列16G U盘一个(官方推荐) 3.MiniPwner的脚本(点这里 下载,minipwner-overlay_2.0.0.tar)
0x02 格式化U盘: 1.格式化为两个分区,一个500M的分区用与SWAP 2.推荐使用linux下fdisk或GParted来完成分区
分区1 = 500M SWAP
0x03 刷入openwrt 1.下载用于TP-LINK MR3040的openwrt固件(点这里 )
2.启动路由器并登录http://192.168.0.1 (默认用户名密码均为admin)
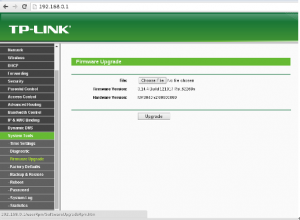
3.选择System Tools —- Firmware Upgrade
4.选择openwrt固件,点击Upgrade刷入openwrt固件(不能断电)
5.路由器升级完毕后,IP地址为192.168.1.1
0x04 配置U盘启动 1.使用telnet连接192.168.1.1
2.passwd设置root密码(root密码设置后telnet将无法登陆,使用ssh连接即可)
3.配置路由器的网络并下载安装以下软件包(网络配置路径:/etc/config/network)
1 2 3 4 5 6 kmod-scsi-core kmod-usb-storage block-mount kmod-lib-crc16 kmod-crypto-hash kmod-fs-ext4
4.将U盘插入路由器的USB口并重启路由器
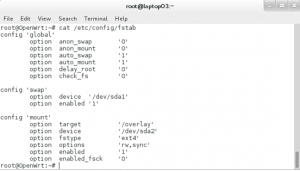
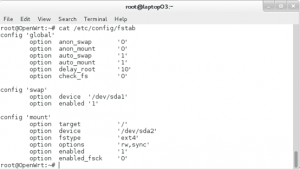
5.登陆路由器并修改/etc/config/fstab文件,如下图
6.运行以下命令将系统copy到U盘
1 2 3 4 5 6 mkdir -p /tmp/cproot mount --bind / /tmp/cproot mkdir /mnt/sda2 mount /dev/sda2 /mnt/sda2 tar -C /tmp/cproot -cvf - . tar -C /mnt/sda2 -xf - umount /tmp/cproot
7.再次修改/etc/config/fstab文件,使设备从U盘启动
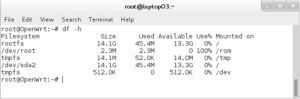
8.重启路由器,通过df -h命令检查是否从U盘启动
9.如果上述步骤一切正常,你就可以在U盘上安装任何你想要的软件包了。
0x05 安装MiniPwner 1.安装一下软件包(部分为默认安装)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 libpcap\_1.5.3-1\_ar71xx libstdcpp\_4.8-linaro-1\_ar71xx libpthread\_0.9.33.2-1\_ar71xx zlib\_1.2.8-1\_ar71xx libopenssl\_1.0.1j-1\_ar71xx libbz2\_1.0.6-1\_ar71xx bzip2\_1.0.6-1\_ar71xx terminfo\_5.9-1\_ar71xx libnet1\_1.1.6-1\_ar71xx libpcre\_8.35-2\_ar71xx libltdl\_2.4-1\_ar71xx libncurses\_5.9-1\_ar71xx librt\_0.9.33.2-1\_ar71xx libruby\_1.9.3-p545-1\_ar71xx wireless-tools\_29-5\_ar71xx hostapd-common-old\_2014-06-03.1-1\_ar71xx kmod-madwifi\_3.10.49+r3314-6\_ar71xx ruby\_1.9.3-p545-1\_ar71xx uclibcxx\_0.2.4-1\_ar71xx libnl\_3.2.21-1\_ar71xx libcap\_2.24-1\_ar71xx libreadline\_6.2-1\_ar71xx libdnet\_1.11-2\_ar71xx libdaq\_1.1.1-1\_ar71xx libuuid\_2.24.1-1\_ar71xx libffi\_3.0.13-1\_ar71xx python-mini\_2.7.3-2\_ar71xx openssl-util\_1.0.1j-1\_ar71xx kmod-tun\_3.10.49-1\_ar71xx liblzo\_2.08-1\_ar71xx libevent2-core\_2.0.21-1\_ar71xx libevent2-extra\_2.0.21-1\_ar71xx libevent2-openssl\_2.0.21-1\_ar71xx libevent2-pthreads\_2.0.21-1\_ar71xx libevent2\_2.0.21-1\_ar71xx aircrack-ng\_1.1-3\_ar71xx elinks\_0.11.7-1\_ar71xx ettercap\_NG-0.7.3-2\_ar71xx karma\_20060124-1\_ar71xx kismet-client\_2010-07-R1-2\_ar71xx kismet-drone\_2010-07-R1-2\_ar71xx kismet-server\_2010-07-R1-2\_ar71xx nbtscan\_1.5.1\_ar71xx netcat\_0.7.1-2\_ar71xx nmap\_6.46-1\_ar71xx openvpn-easy-rsa\_2013-01-30-2\_ar71xx openvpn-openssl\_2.3.6-1\_ar71xx perl\_5.20.0-6\_ar71xx samba36-client\_3.6.24-1\_ar71xx samba36-server\_3.6.24-1\_ar71xx snort\_2.9.2.2-3\_ar71xx tar\_1.23-1\_ar71xx tcpdump\_4.5.1-4\_ar71xx tmux\_1.9a-1\_ar71xx yafc\_1.1.1-2\_ar71xx wget\_1.16-1\_ar71xx python\_2.7.3-2\_ar71xx vim\_7.3-1\_ar71xx unzip\_6.0-1\_ar71xx
2.上传MiniPwner 安装脚本到/tmp 目录(上面下载到的minipwner-overlay_2.0.0.tar)
3.解压并运行setup.sh。
4.重启路由器,你就得到了一个MiniPwner